Hello and welcome back this time we'll see crafty ways of escaping bash and PowerShell I really wanted to talk about one of my favourite characters the escape character and how it relates to base64 encoding in PowerShell so the thing about escaping is it's delightful and if I were to just quote Wikipedia I would say
"An escape character is a character that invokes an alternative interpretation on subsequent characters in a character sequence."
ESCAPE CHARACTERS:
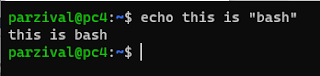
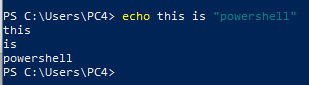
Right so quotation marks aren't the only special characters that you might need to escape in bash you're gonna find Bang( ! ), quote( " ), dollar( $ ), pound( £ ), amp( & ) so many others, The same thing with PowerShell.
Here's a fun little trick that you can use to forego the entire situation at least in PowerShell and that is to use an encoded command Powershell accepts encoded command which states that it accepts a base64 encoded string version of a command which is sort of Microsoft saying hey escaping is hard so just encode it a different way.
BASE64:
Now if you're not familiar with Base64 it's just a simple way of representing any arbitrary binary data in an ASCII format assembly you get 64 simple printable characters then you just choose them to represent stuff. so according to wikipedia
Base64 is a group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation.
It's basically a way of encoding arbitrary binary data in ASCII text. It takes 4 characters per 3 bytes of data, plus potentially a bit of padding at the end.
Essentially each 6 bits of the input is encoded in a 64-character alphabet. The "standard" alphabet uses A-Z, a-z, 0-9 and + and /, with = as a padding character. There are URL-safe variants. WiKi
HID Attack:
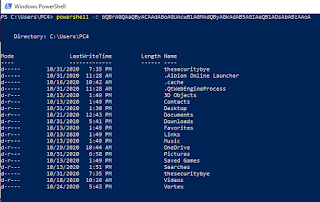
We just learned that PowerShell will accept base64-encoded commands which are made up of those characters you don't actually need to escape then you might imagine that you could put those things together and just take the headache out of this stuff completely so as an example if we were to make like this payload here that creates a new directory called thesecuritybye and then does a directory listing we get actually base64 those and sent him off to powershell.
Okay so open up your terminal and type
echo "mkdir thesecuritybye;ls" | iconv -t utf-16le | base64
It actually converts that over to utf-16 encoding which is what PowerShell is going to be expecting and then by piping that to base64 well we get that simple plaintext ascii that if we copy it back over onto a powershell and type powershell -E yourbase64.








0 Comments